Secure, Sandboxed and Ungoogled Chromium
This blog post explains my approach for a properly sandboxed web browser on a Linux desktop.
Apart from the operating system you are using, the web browser is probably the most critical piece of software that you are using. To reduce the impact of security vulnerabilities, applications should have as few permissions as possible. With the large attack surface of web browsers this is especially important. After reading this very interesting blog post I decided to switch from firefox to a Chromium-based browser.
ungoogled-chromium
There are many web-browsers based on Chromium, including Google Chrome, Microsoft Edge and Vivaldi. I decided to go for ungoogled-chromium, particularly because it is a regularly maintained project, relatively large, they disable functionality specific to Google domains and updates from Chromium are available quickly. However it does not otherwise modify the behaviour of Chromium.
Sandbox
While Chromium provides sandboxing of the different processes (see the previously mentioned blog post), I generally prefer to also sandbox applications as a whole. This should be easy to use and work the same for all applications. While Android has a proper integrated permission system, on a Linux desktop there is no comparable integrated system.
Flatpak
However with Flatpak there exists a package management system, which sandboxes at least those applications that are installed from it. ungoogled-chromium can be installed from flathub.org. You can also install other web-browsers based on Chromium like Vivaldi from Flatpak, so from now on I will just refer to ungoogled-chromium as Chromium. I tested that the steps are the same at least for Vivaldi. With Flatseal it is possible to modify the permissions of Flatpak applications using a graphical user interface.
X11
In Flatseal we can see that Chromium has access to the X11 windowing system.
Allowing X11 kind of completely defeats the purpose to sandbox the application itself (again see the previously mentioned blog post).
However when just disabling X11 Chromium does not start anymore.
This can be solved by starting Chromium with X11 enabled, then going to about://flags (or vivaldi:flags) and setting the Preferred Ozone platform to Wayland.
Now we can disable X11 and Inter-process communications (ipc) and restart Chromium.
Et voilà, Chromium starts successfully without access to X11!
Smart cards
By default Chromium has access to the smart cards socket, if you do not have any, you can disable access to this socket.
Printing
By default Chromium has access to the Printing system socket, however I was still able to list my printers, so maybe you do not need access to it. This might be because Chromium can access the local CUPS server over the network anyway (http://localhost:631/).
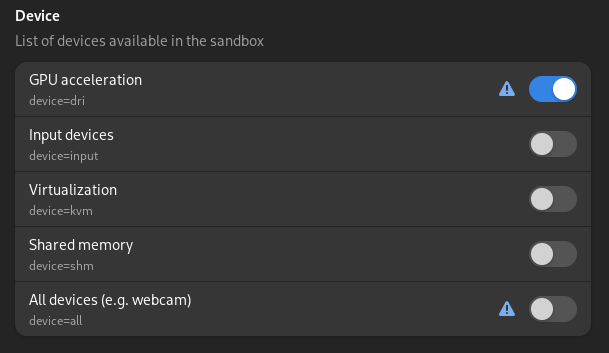
Devices
By default Chromium has access to all devices, which you can disable.
This also removes access to GPU acceleration, which is fine as long as you do not use it.
However you can also instead enable the GPU acceleration again separately (device=dri).
You can verify whether the GPU acceleration works correctly on the page chrome://gpu/.
This also disables access to the camera.
The proper way to fix this would probably be for the browser to access the camera portal of flatpak.
Filesystem
While ungoogled-chromium allows access to all files in the home directory of the user, Vivaldi has a list of folders it has access to by default, as shown here:
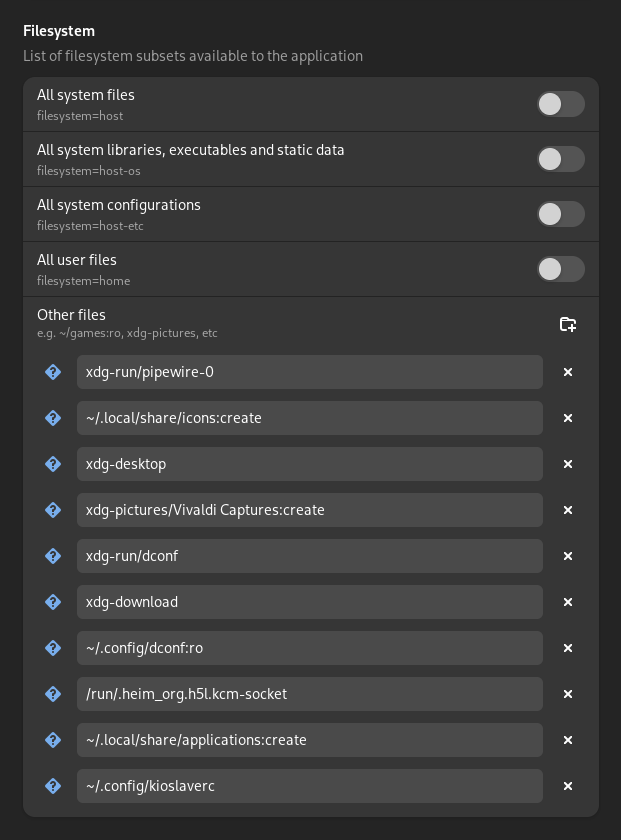
I remove the general access to all files from ungoogled-chromium and add only those accesses that I actually need.
For me that is just xdg-download.
Some entries in vivaldi like xdg-run/pipewire-0 that should be used to access pipewire, are apparently not used, as pulseaudio is used for audio, screensharing works through the portal and accessing the camera does not work anyway.